The CYCL Platform delivers a comprehensive Cloud Detection & Response (CDR) solution combined with our 24/7 AI SOC service. Together they provide the visibility, detection, and expert intervention your cloud infrastructure needs to stay secure, compliant, and resilient. With both agentless, and AI agent capabilities, CYCL ensures full-stack coverage across cloud platforms without slowing your teams or workloads.
CDR Plus AI SOC Technology and Expertise Combined
Our technology is powerful but it is our people who complete the solution. CYCL’s SOC experts work alongside the platform to deliver continuous monitoring, deep investigations, and rapid threat response. This combination of AI and human intelligence ensures your cloud is actively defended at all times.
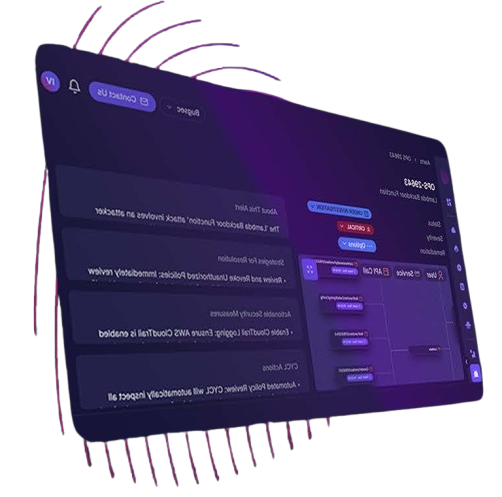
As cloud threats evolve, attackers increasingly exploit compromised non-human identities and subtle access patterns. CYCL’s Behavioral Detection engine uses AI-powered User and Entity Behavior Analytics (UEBA) to continuously profile human & machine users, assets, and services while learning from real-time activities to detect anomalies with precision.
This dynamic approach minimizes false positives and identifies risks tailored to your cloud’s unique behavioral fingerprint.
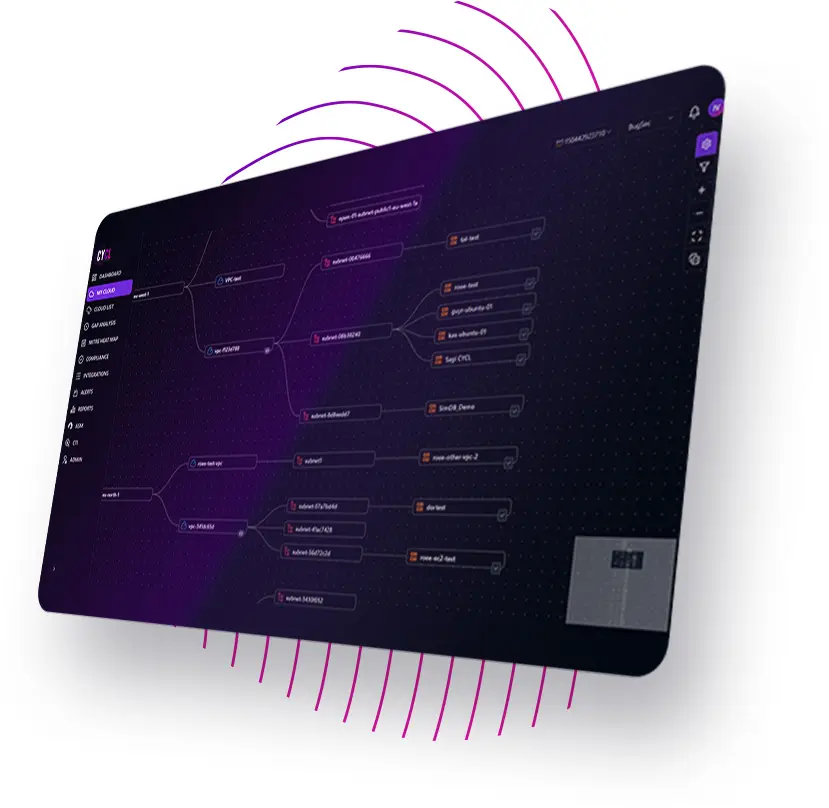
CYCL’s Discovery Map provides deep insight into all your cloud assets across multiple providers and environments, keep you informed of rapid cloud changes and shadow IT. Supporting both agentless and AI agent, it enables continuous monitoring to detect potential threats without impacting performance while ensuring seamless security at scale.
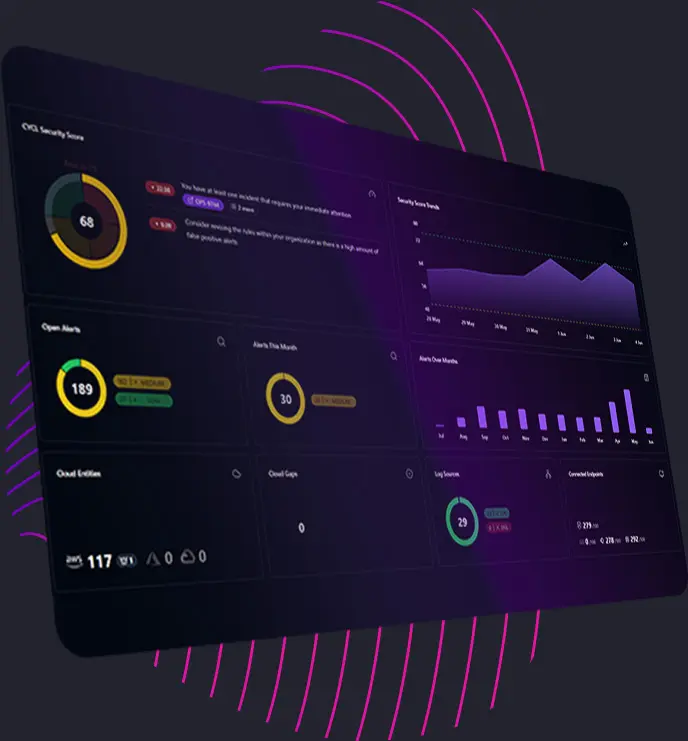
The CYCL Security Score dynamically assesses your cloud security posture against known vulnerabilities and real-time threat intelligence. It helps prioritize remediation efforts while guiding your teams to strengthen defenses efficiently and measurably.
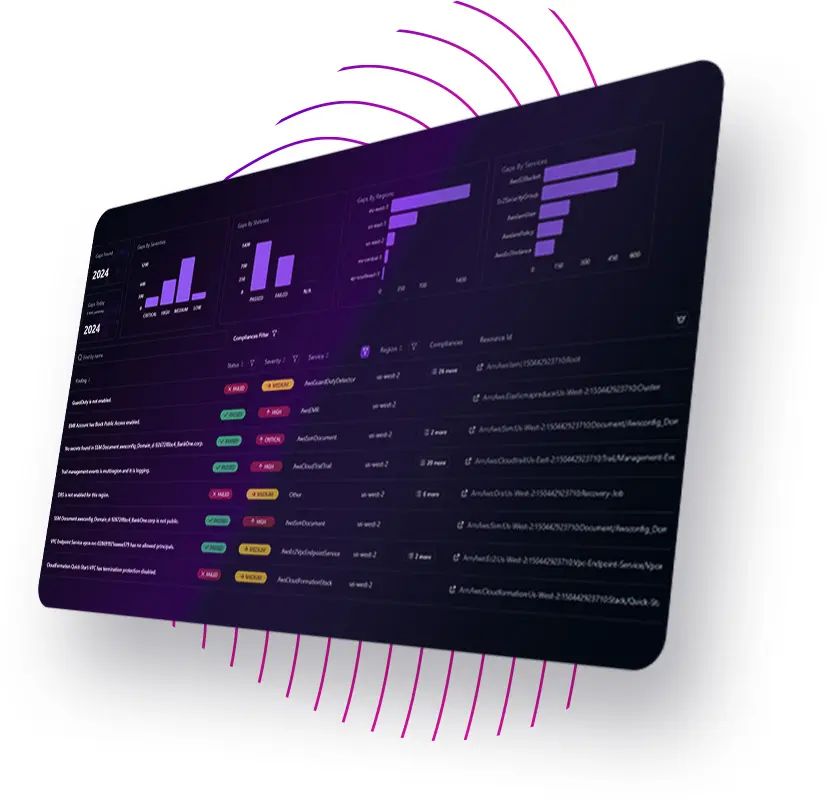
Our Gap Analysis rigorously evaluates your cloud configurations against leading benchmarks from AWS, NIST, and MITRE. It identifies misconfigurations, , and operational weaknesses while providing clear actionable insights for remediation.
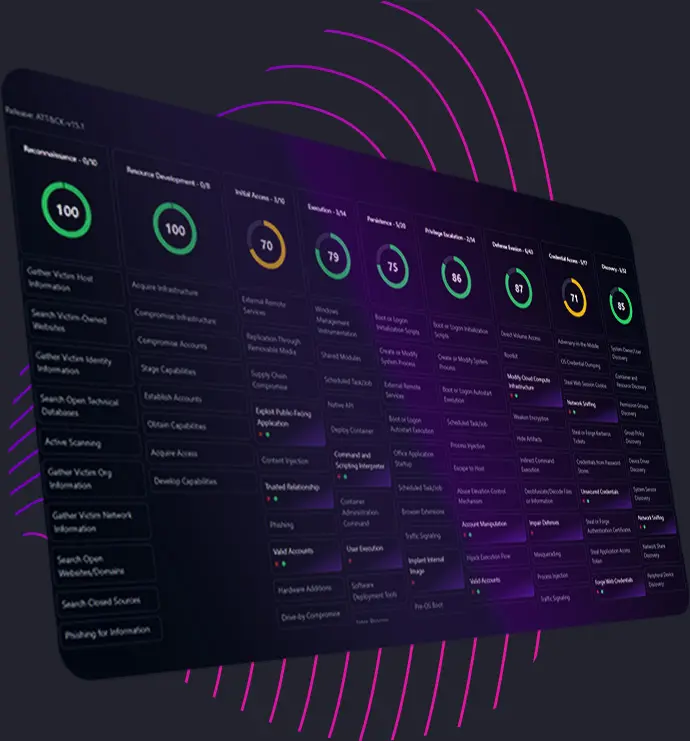
CYCL integrates the MITRE ATT&CK framework, aligning detection and response strategies with globally recognized tactics and techniques. This structured methodology ensures advanced threat coverage across your cloud environments.
Stay ahead of regulatory requirements with CYCL’s Compliance Assurance module. The platform continuously monitors for alignment with standards like GDPR, HIPAA, PCI-DSS, and SOC 2, keeping your cloud environments compliant and audit ready with up-to-date documentation.

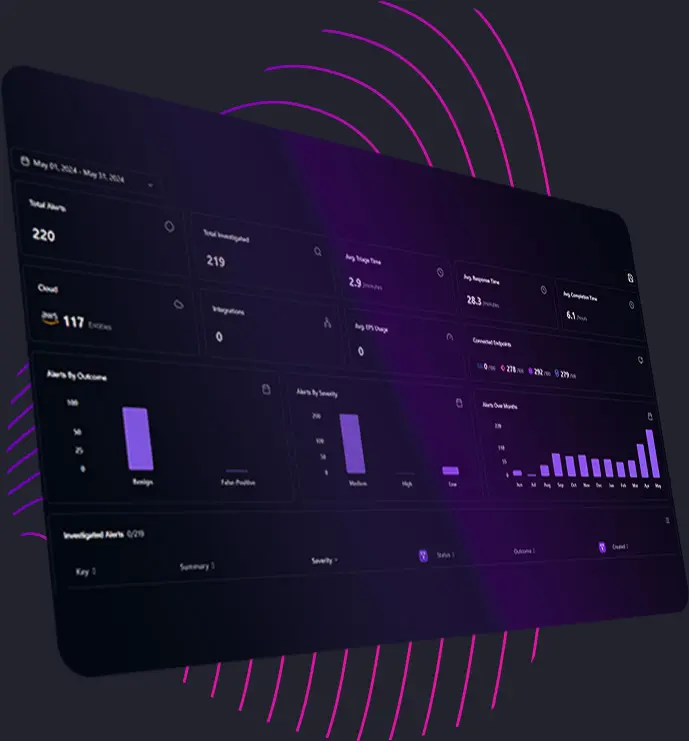
Auto-Pilot leverages our AI agent to automate threat detection, response, and remediation. It dynamically adjusts security controls in real time based on evolving threats while reducing manual overhead and enhancing operational efficiency.
CYCL provides native protection for Kubernetes clusters and workloads with real-time threat detection, deep visibility, and detailed gap analysis. It ensures secure operations without adding unnecessary complexity for your DevOps and security teams.


Mid-sized enterprises face a critical security gap: 67% experienced cloud security incidents in 2024 (Verizon DBIR 2024), with average breach costs reaching $4.88 million (IBM’s 2024 Cost of Data Breach Report). Yet traditional security approaches fall short in dynamic cloud environments where attacks unfold in minutes, not hours.